Thursday, June 20, 2013
BRAZIL - the world cup - the olympics... and you
Consider how the decisions are made to spend this money. Consider: the Roman Empire had its colosseum - it didn't prevent the collapse of the empire.
Tuesday, June 18, 2013
Whistle Blowing in the Orwellian Universe: from Wired Magazine
The Whistleblower’s Guide to the Orwellian Galaxy: How to Leak to the Press
- By Nicholas Weaver
Editor’s Note: An earlier version of this article ran in Wired Opinion last month (“Hear Ye, Future Deep Throats: This Is How to Leak to the Press”). It has been updated given recent events and reflects the author’s new findings about government recording of mail.
Daniel Ellsberg, Mark Felt, Jeffrey Wigand, Sherron Watkins, Bradley Manning, and now… Edward Snowden. (He’s just the latest informant caught in the web of government administrations that view George Orwell’s 1984 as an operations manual.)
But while the list of government (and corporate) whistleblowers continues to grow, their options for leaking continue to shrink. It is, as one commenter noted, “a dangerous time to be right when the government is wrong.” We now live in a world where public servants informing the public about government behavior or wrongdoing must practice the tradecraft of spies and drug dealers à la The Wire. Even the head of the CIA can’t email his mistress without being identified by the FBI. And privately collected data isn’t immune, either; highly sensitive metadata is particularly vulnerable thanks to the Third Party Doctrine.
So how can one safely leak information to the press, let alone coordinate a Deep Throat-style meetup? The obvious choices: email, phone, and mail … but you’ve got to be really careful. Here’s a guide.


 The CIA supposedly already provided
a guide to secure email, which the Russian Federal Security Service
(FSB) translated back to English — convenient, given the situation we
now find ourselves in.
The CIA supposedly already provided
a guide to secure email, which the Russian Federal Security Service
(FSB) translated back to English — convenient, given the situation we
now find ourselves in.
Get a dedicated computer or tablet: the cheapest Windows laptop will do. And pay cash, as our normal laptops have a host of automatic synchronization and similar services. Our personal web browsers also contain all sorts of location-identifying cookies. Even if you’re logged in to but don’t actually visit Facebook’s home page, a subpoena to Facebook can still reveal where you connect and what pages you visit — every “Like” button reports to Facebook that you are visiting that particular page, at a particular time, from a particular IP address.
Leave your cellphone, your normal computer, and your metro card (like SmarTrip) at home: anything that speaks over a wireless link must stay behind. Then go to a coffee shop that has open Wi-Fi, and once there open a new Gmail account that you will only use to contact the press and only from the dedicated computer. When registering, use no personal information that can identify you or your new account: no phone numbers, no names.
Don’t forget: if you get anything at the cafe, or take public transit, pay cash. Be prepared to walk a bit, too; you can’t stay close to home for this.
Of course, the job still isn’t finished. When you are done you must clear the browser’s cookies and turn off the Wi-Fi before turning off the computer and removing the battery. The dedicated computer should never be used on the network except when checking your press-contact account and only from open Wi-Fi connections away from home and work.
By the way, I would personally look for a store with security cameras that look old — a continuous tape or similar setup — since once the FBI has the number, the next step is to contact the store that sold the phone. Alternatively, you can get someone else to walk into the store and buy it for you.
You now own your very own “burner” phone — remember The Wire? – and this phone must remain off with the battery removed at all times. Because every active cellphone is effectively a continuous GPS, monitoring your location and feeding the information to the phone company which retains this information for weeks, months, even years. Just a warrant-step away.
Now, to use the phone … Once again, go to a different location without carrying your normal devices, turn on the phone, check your voicemail, make your call, turn it off again, and pull out the battery. Your phone calls are now (hopefully) anonymous so that when the FBI leak-hunt starts, there is no trail for them to follow.
Of course, the burner laptop or phone could still identify you if it’s ever found, as they both contain network identifiers built into the hardware. So if you ever need to abandon your device, first wipe the device back to its factory fresh configuration using any “secure erase” options available, then take a hammer and break the device. Put it in some other piece of trash (like an empty McDonald’s sack), go for another stroll, and drop in a public trashcan.
But if the feds are already following you, you’re caught anyway, so it doesn’t matter if they catch you taking out the trash instead of finding something when they search your home.
Believing that the U.S. Postal Service recorded specific mail address information only when asked by law enforcement, I had previously argued that there’s no history with mail — and even if there were, it could only be traced to the processing post office.
However, The Smoking Gun spotted — buried in an affidavit! — that the U.S. Postal Service records the outside of mail. According to the full affidavit (also available on RECAP; see page 5) the machine used to automate mail operations, the Automated Facer Canceler System, contains a “Mail Isolation Control and Tracking” program that photographs every single piece of mail and maintains this information for future access by law enforcement.
Although there’s no mention of optical character recognition to allow indexing by recipient rather than by postmark, leakers must now assume that the U.S. government is indeed recording the outside of everything we mail. A leaker should therefore access a public postbox in the same way s/he uses a burner phone: Leave all devices behind, walk to a remote postbox, and follow all the other guidelines above. But be sure to include a note to the reporter telling him or her to trash the envelope immediately.
***
All of this may seem like a script for a fictional T.V. show. But such extreme measures are a modern necessity if you want to leak information. Any future Deep Throat needs to follow these sorts of procedures if he or she wishes to talk to the press.
Though just imagine if Mark Felt had to do all of the above when leaking to Woodward and Bernstein. Snowden might have been willing to out himself … but not everyone is.
Miscellaneous Commentary from various people commenting on the post in wired magazine follows:
Don't forget not to use any Windows or Apple OS. Download a Linux
system in source-code format and compile it yourself. Microsoft has now
admitted that they have back-door monitors on all their systems since
1999 and, although they deny it, Apple probably has also.
Leak it to a foreign press agency. Everybody in the US is bought and paid for.Daniel Ellsberg, Mark Felt, Jeffrey Wigand, Sherron Watkins, Bradley Manning, and now… Edward Snowden. (He’s just the latest informant caught in the web of government administrations that view George Orwell’s 1984 as an operations manual.)
But while the list of government (and corporate) whistleblowers continues to grow, their options for leaking continue to shrink. It is, as one commenter noted, “a dangerous time to be right when the government is wrong.” We now live in a world where public servants informing the public about government behavior or wrongdoing must practice the tradecraft of spies and drug dealers à la The Wire. Even the head of the CIA can’t email his mistress without being identified by the FBI. And privately collected data isn’t immune, either; highly sensitive metadata is particularly vulnerable thanks to the Third Party Doctrine.
So how can one safely leak information to the press, let alone coordinate a Deep Throat-style meetup? The obvious choices: email, phone, and mail … but you’ve got to be really careful. Here’s a guide.
The parking garage where Bob Woodward met Mark Felt (Deep Throat). photo: martin_kalfatovic / Flickr
Leaking by Email
Nicholas Weaver
Nicholas
Weaver is a researcher at the International Computer Science Institute
in Berkeley and U.C. San Diego (though this opinion is his own).
He focuses on network security as well as network intrusion detection,
defenses for DNS resolvers, and tools for detecting ISP-introduced
manipulations of a user’s network connection. Weaver received his Ph.D.
in Computer Science from U.C. Berkeley.
Get a dedicated computer or tablet: the cheapest Windows laptop will do. And pay cash, as our normal laptops have a host of automatic synchronization and similar services. Our personal web browsers also contain all sorts of location-identifying cookies. Even if you’re logged in to but don’t actually visit Facebook’s home page, a subpoena to Facebook can still reveal where you connect and what pages you visit — every “Like” button reports to Facebook that you are visiting that particular page, at a particular time, from a particular IP address.
Leave your cellphone, your normal computer, and your metro card (like SmarTrip) at home: anything that speaks over a wireless link must stay behind. Then go to a coffee shop that has open Wi-Fi, and once there open a new Gmail account that you will only use to contact the press and only from the dedicated computer. When registering, use no personal information that can identify you or your new account: no phone numbers, no names.
Don’t forget: if you get anything at the cafe, or take public transit, pay cash. Be prepared to walk a bit, too; you can’t stay close to home for this.
Of course, the job still isn’t finished. When you are done you must clear the browser’s cookies and turn off the Wi-Fi before turning off the computer and removing the battery. The dedicated computer should never be used on the network except when checking your press-contact account and only from open Wi-Fi connections away from home and work.
Leaking Over the Phone
Again, start by leaving all electronic devices at home. Go to a small liquor store in a low-income neighborhood, and buy a pre-paid cellphone (TracPhone or similar) with cash. Make sure it has enough airtime to not expire for a few months — T-mobile prepaid is particularly good since the pay-as-you-go plan doesn’t expire for a full year if you buy $100 of airtime.By the way, I would personally look for a store with security cameras that look old — a continuous tape or similar setup — since once the FBI has the number, the next step is to contact the store that sold the phone. Alternatively, you can get someone else to walk into the store and buy it for you.
You now own your very own “burner” phone — remember The Wire? – and this phone must remain off with the battery removed at all times. Because every active cellphone is effectively a continuous GPS, monitoring your location and feeding the information to the phone company which retains this information for weeks, months, even years. Just a warrant-step away.
Now, to use the phone … Once again, go to a different location without carrying your normal devices, turn on the phone, check your voicemail, make your call, turn it off again, and pull out the battery. Your phone calls are now (hopefully) anonymous so that when the FBI leak-hunt starts, there is no trail for them to follow.
Of course, the burner laptop or phone could still identify you if it’s ever found, as they both contain network identifiers built into the hardware. So if you ever need to abandon your device, first wipe the device back to its factory fresh configuration using any “secure erase” options available, then take a hammer and break the device. Put it in some other piece of trash (like an empty McDonald’s sack), go for another stroll, and drop in a public trashcan.
But if the feds are already following you, you’re caught anyway, so it doesn’t matter if they catch you taking out the trash instead of finding something when they search your home.
Leaking by Mail
Investigative journalist Julia Angwin of the Wall Street Journal pointed out that physical mail, dropped in a random post-box with a bogus return address, is perhaps the best way for anonymous one-way communication. Perhaps the best use of mail is simply to send the reporter a burner phone pre-programmed to only call your burner.Believing that the U.S. Postal Service recorded specific mail address information only when asked by law enforcement, I had previously argued that there’s no history with mail — and even if there were, it could only be traced to the processing post office.
However, The Smoking Gun spotted — buried in an affidavit! — that the U.S. Postal Service records the outside of mail. According to the full affidavit (also available on RECAP; see page 5) the machine used to automate mail operations, the Automated Facer Canceler System, contains a “Mail Isolation Control and Tracking” program that photographs every single piece of mail and maintains this information for future access by law enforcement.
Although there’s no mention of optical character recognition to allow indexing by recipient rather than by postmark, leakers must now assume that the U.S. government is indeed recording the outside of everything we mail. A leaker should therefore access a public postbox in the same way s/he uses a burner phone: Leave all devices behind, walk to a remote postbox, and follow all the other guidelines above. But be sure to include a note to the reporter telling him or her to trash the envelope immediately.
***
All of this may seem like a script for a fictional T.V. show. But such extreme measures are a modern necessity if you want to leak information. Any future Deep Throat needs to follow these sorts of procedures if he or she wishes to talk to the press.
Though just imagine if Mark Felt had to do all of the above when leaking to Woodward and Bernstein. Snowden might have been willing to out himself … but not everyone is.
Miscellaneous Commentary from various people commenting on the post in wired magazine follows:
Rule Number One: Only leak to the US Press when a republican occupies the White House.
Rule Number Two: All governments use force of suppress descent.
Rule Number Three: When the people fear the government there is Tyranny.
Rule Number Four: When the government fears the people there is Liberty.
VPNs and tor would help as well for one way communication.
Rule Number Two: All governments use force of suppress descent.
Rule Number Three: When the people fear the government there is Tyranny.
Rule Number Four: When the government fears the people there is Liberty.
Leaking by mail is a BAD IDEA.
- The envelope is tracked.
- Using ANY modern printer leaves identifiable micro ID marks on the printed page, tracking it back to it's point of origin.
If you were to follow the advice on electronics, and do a bit of research on computer security (like using BackTrack5 on a USB/SD card), you might have the tiniest chance in hell of not getting caught. The FBI/CIA/NSA are a lot better at their job than you would be at playing secret agent.
The real question you need to ask yourself: Is doing the 'right thing' worth being water-boarded and prison raped?
Don't go to the ATM just before you start leaking your information. It could be the piece of the puzzle that puts everything else together. Collect the cash you're going to use over time.
- The envelope is tracked.
- Using ANY modern printer leaves identifiable micro ID marks on the printed page, tracking it back to it's point of origin.
If you were to follow the advice on electronics, and do a bit of research on computer security (like using BackTrack5 on a USB/SD card), you might have the tiniest chance in hell of not getting caught. The FBI/CIA/NSA are a lot better at their job than you would be at playing secret agent.
The real question you need to ask yourself: Is doing the 'right thing' worth being water-boarded and prison raped?
Don't go to the ATM just before you start leaking your information. It could be the piece of the puzzle that puts everything else together. Collect the cash you're going to use over time.
VPNs and tor would help as well for one way communication.
It's a matter of jurisdiction and impact - if you turn out to be located in Nigeria, Belarus or some other place where the authorities are uninterested in bringing charges. There's also little value in tracking them down unless they've dinged someone powerful for something of great value.
You may want to change the MAC address of the WiFi NIC after each WiFi use as well, as there is probably a record of your connection with the open hotspot, linked to the NIC's MAC address, and then there is probably a record about which NIC with which MAC address was put into which computer and where was that computer sold. The vendor may then remember a nerdy looking man with glasses and a fledgling beard.
There may be another backdoor in the hardware, perhaps Cisco or whoever manufactured your WiFi NIC, has - on government demand - put in some extra data that is communicated or collected or a chip that remembers which access points you have connected to, and perhaps this chip uploads this information on a regular basis to a certain server that is screened by the CIA.
"The dedicated computer should never be used on the network except when checking your press-contact account"
Never ever log into the same account. They monitor newspapers and once you log in with the same username or send to the same e-mail address they can locate your IP-address/location within seconds or provide you with a faked email service.
Don't even try to establish a two-way communication, just drop the material physically. If you are going to print it out, beware that most printers write identifications numbers that can be tracked
Beware of ~ set up internet cafes where you may be exposed to an email interception programme and key-logging software to spy on delegates use of computers.
Dont go back to the same cafe/brand of cafe after the first email.
Never trust any generation of MS or Apple filesystem/OS.
Something might be waiting for you to log in again.
And...Mind the cameras - even when sending an email from some coffee shop, there is a chance you get picked up by CCTV on your way there. If the authorities have any other indication that it could be you, this might be enough for them to connect the dots.
Buy a wireless dongle using cash. Turn off the laptop wireless completely and use the dongle for wireless, then if the ISP captures the MAC address it will be for the dongle that you dump on the way home.
Search on MAC spoofing.There should be software for
every platform that allows you to alter the MAC address your device
exposes via wireless. Change it for each new leak connection.
Many laptops could be direct from a corporate or gov bulk sale. The barcode on the back is for a MAC and laptop serial number. Once your leaking MAC is "seen" online, tracking it back as corporate or gov unit and its sale might be easy. You are then on CCTV in that part of the city buying a laptop. They have your face.
Switch to Linux. Those systems have had the ability for years to change your MAC number from the keyboard.
When you are done ... turn off the Wi-Fi before turning off the computer and removing the battery' to prevent the computer from automatically logging into a network next time it's turned on, which might or might not be in a secure location. By getting ahead of this cycle, you avoid mistakes, or turn the mistake of turning your laptop on in one of your locations into a trivial one, rather than a game-ender.
And then there is this rather interesting submision:
It takes a hero to act without regard to the suffering he will endure at the hands of those who are ill-informed or in pursuit of a dictatorial agenda. No wonder heroes are generally found among the young. The old are too self-interested and afraid; they'll endure anything, permit anything, perpetrate anything in the hopeless endeavor to avoid scrutiny and preserve their deluded sense of personal security. That is why it is always a nation's youth that constitutes its conscience.
Moreover, you may not have noticed, but education is as much a part of the "real" world as the witlessness of the unschooled and the untaught. Maybe if you lived in the "real" world you would understand things better. But you obviously live in a fantasy world. This country is made stronger by those who refuse tyranny, not pettifogging fools who can't distinguish between legitimate security interests and despotism. Your comparison of Snowden to the Rosenbergs is ludicrous, it demonstrates nothing so much as your own ignorance. Those countries you name have known for years pretty much the full extent of domestic spying in the US. This will probably come as a shock to you, but they use virtually the same technologies for the same purposes, in some instances that which may actually be superior to ours. Snowden leaked information to the domestic public which was hidden only from the domestic public. He did not pass information to a foreign enemy. Indeed, as only a young man would, he relinquished a bright and comfy future terrorizing his fellow countrymen (yep, that's what the NSA and its sister agencies do) in favor of doing what is in the best interests of his fellow countrymen.
Those who engage in domestic spying, those who amass and analyze the contents of private communications and data associated with such communications in the absence of specific information rising to the level of probable cause, those who resort to clearly unconstitutional "blanket warrants," and those who acquiesce in those activities are they who represent the most insidious threat to liberty. Every policy maker who participated in or knew of such spying and took no affirmative action to expose and halt it should be hung on the public square with marching bands in attendance.
As a final word, I point out that despite your grandiose airs you possess the same dearth of knowledge as those who you so blithely disparage. Not only do you know nothing worth leaking, you have nothing worth saying or writing.
Diplomatic challenges do not constitute a rational basis for dismantling the US Constitution.
The assertion that the Constitution is outdated and unsuitable for modern circumstances simply will not withstand the test of history. To suggest that the US government needs or (as has been discussed elsewhere) can even effectively utilize "blanket warrants" for the proffered purposes is ludicrous. We must not succumb to the fatalistic assumption that the surrender of our freedom is a prerequisite to the preservation of our way of life. Such an assumption is self-defeating. Indeed, if we accept surrender then our way of life ceases to exist.
Government will always abuse its power. That is the nature of the beast. If you disagree, prove me wrong. Just give me an single example of a government power that was not, eventually, given enough time, misused to hurt some of our citizens.
Many laptops could be direct from a corporate or gov bulk sale. The barcode on the back is for a MAC and laptop serial number. Once your leaking MAC is "seen" online, tracking it back as corporate or gov unit and its sale might be easy. You are then on CCTV in that part of the city buying a laptop. They have your face.
Switch to Linux. Those systems have had the ability for years to change your MAC number from the keyboard.
When you are done ... turn off the Wi-Fi before turning off the computer and removing the battery' to prevent the computer from automatically logging into a network next time it's turned on, which might or might not be in a secure location. By getting ahead of this cycle, you avoid mistakes, or turn the mistake of turning your laptop on in one of your locations into a trivial one, rather than a game-ender.
And then there is this rather interesting submision:
It takes a hero to act without regard to the suffering he will endure at the hands of those who are ill-informed or in pursuit of a dictatorial agenda. No wonder heroes are generally found among the young. The old are too self-interested and afraid; they'll endure anything, permit anything, perpetrate anything in the hopeless endeavor to avoid scrutiny and preserve their deluded sense of personal security. That is why it is always a nation's youth that constitutes its conscience.
Moreover, you may not have noticed, but education is as much a part of the "real" world as the witlessness of the unschooled and the untaught. Maybe if you lived in the "real" world you would understand things better. But you obviously live in a fantasy world. This country is made stronger by those who refuse tyranny, not pettifogging fools who can't distinguish between legitimate security interests and despotism. Your comparison of Snowden to the Rosenbergs is ludicrous, it demonstrates nothing so much as your own ignorance. Those countries you name have known for years pretty much the full extent of domestic spying in the US. This will probably come as a shock to you, but they use virtually the same technologies for the same purposes, in some instances that which may actually be superior to ours. Snowden leaked information to the domestic public which was hidden only from the domestic public. He did not pass information to a foreign enemy. Indeed, as only a young man would, he relinquished a bright and comfy future terrorizing his fellow countrymen (yep, that's what the NSA and its sister agencies do) in favor of doing what is in the best interests of his fellow countrymen.
Those who engage in domestic spying, those who amass and analyze the contents of private communications and data associated with such communications in the absence of specific information rising to the level of probable cause, those who resort to clearly unconstitutional "blanket warrants," and those who acquiesce in those activities are they who represent the most insidious threat to liberty. Every policy maker who participated in or knew of such spying and took no affirmative action to expose and halt it should be hung on the public square with marching bands in attendance.
As a final word, I point out that despite your grandiose airs you possess the same dearth of knowledge as those who you so blithely disparage. Not only do you know nothing worth leaking, you have nothing worth saying or writing.
Diplomatic challenges do not constitute a rational basis for dismantling the US Constitution.
The assertion that the Constitution is outdated and unsuitable for modern circumstances simply will not withstand the test of history. To suggest that the US government needs or (as has been discussed elsewhere) can even effectively utilize "blanket warrants" for the proffered purposes is ludicrous. We must not succumb to the fatalistic assumption that the surrender of our freedom is a prerequisite to the preservation of our way of life. Such an assumption is self-defeating. Indeed, if we accept surrender then our way of life ceases to exist.
Government will always abuse its power. That is the nature of the beast. If you disagree, prove me wrong. Just give me an single example of a government power that was not, eventually, given enough time, misused to hurt some of our citizens.
Subscribe to:
Comments (Atom)
Useful Links
- Mount Gox - Bitcoin exchange
- Reggie Middleton's Rapier Analysis
- Ontario Rivers Alliance
- Geodesic Dome Construction
- Canadian Disaster Preparedness
- Globe and Mail
- Chris' The Weekly Telegram
- Michael Rupert of CollapseNet
- Max Keiser
- Nicole Foss Blog - the automatic earth
- Peak Moment Discussions
- Scotia Mocatta Bullion Store
- Dimitry Orlov - Peak Moment Discussions
- Jims's ISFCR Blog
- Jenny Right Side Blog
- Scott Sorensen
Alternative Energy Sites I like
The Queen is not amused!

http://www.ispeakforcanadianrivers.ca/
The Ashlu river: it could happen to you

Whitewater Ontario

Working Hard to Protect Canada's Paddling Resources
Whitewater Ontario - Mission Statement
It is Whitewater Ontario’s mission to support the whitewater paddling community through the promotion, development and growth of the sport in its various disciplines.
We accomplish this through the development of events, resources, clubs, and programs for personal and athletic development, regardless of skill level or focus, to ensure a high standard of safety and competency;
We advocate safe and environmentally responsible access and use of Ontario’s rivers.
Whitewater Ontario is the sport governing body in the province, and represents provincial interests within the national body Whitewater Canada and the Canadian Canoe Association
http://www.whitewaterontario.ca/page/mission.asp
Kipawa, Tabaret, and Opemican
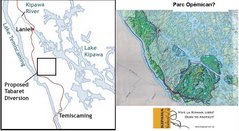
If Hydro Quebec is not actively pursuing Tabaret what is that bite out of Opemican for?
Kipawa Dam: After

Laniel Dam at 2006 Rally
Where is the Kipawa
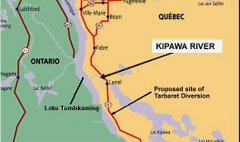
Kipawa flows into lake Temiskamingue, running from Kipawa Lake, under hwy 101 in Quebec
Kipawa Dam

laniel dam at 2004 River Rally
Tabaret is a Bad Idea
About the Kipawa
The best thing paddlers can do to help the cause of the Kipawa:
1. attend the rally and bring others including non paddlers to attend and buy beer and have fun
2. write your MP /MNA and raise the issue and post your objections -1 letter = 200 who didn't write
3. Write Thierry Vandal the CEO of Hydro Quebec strongly opposing the 132 MW standard decrying the use of "diversion" as the most environmentally inappropriate method of power production
4. Write Jean Charest, Premier of Quebec protesting that either the algonquin or the tabaret project will eliminate all other values on the Kipawa River by turning it into a dry gulch.
5. See if you can get other allied groups interested by showing your own interest, ie the Sierra Defense Fund, Earthwild, MEC, and so on.
6. Demand further consultation
7. Currently we are at the point where we need to sway public opinion and raise awareness.
However, if all else fails, don't get mad, simply disrupt, foment, and protest . The Monkey Wrench Gang.
Have you read Edward Abbey?
Important Addresses
CEO,Hydro Québec, 75 boul René Levesque, Montreal, P.Q., H2Z 1A4Caille.andre@hydro.qc.ca
The best thing paddlers can do to help the cause of the Kipawa:
1. attend the rally and bring others including non paddlers to attend and buy beer and have fun
2. write your MP /MNA and raise the issue and post your objections -1 letter = 200 who didn't write
3. Write Thierry Vandal the CEO of Hydro Quebec strongly opposing the 132 MW standard decrying the use of "diversion" as the most environmentally inappropriate method of power production
4. Write Jean Charest, Premier of Quebec protesting that either the algonquin or the tabaret project will eliminate all other values on the Kipawa River by turning it into a dry gulch.
5. See if you can get other allied groups interested by showing your own interest, ie the Sierra Defense Fund, Earthwild, MEC, and so on.
6. Demand further consultation
7. Currently we are at the point where we need to sway public opinion and raise awareness.
However, if all else fails, don't get mad, simply disrupt, foment, and protest . The Monkey Wrench Gang.
Have you read Edward Abbey?
Important Addresses
CEO,Hydro Québec, 75 boul René Levesque, Montreal, P.Q., H2Z 1A4Caille.andre@hydro.qc.ca
Tabaret is a Bad Idea (Part Two)
Les Amis de la Riviere Kipawa is poised to use an application to the Federal Court to issue a Writ of Mandamus to ensure the Minster does what he is supposed to do, protect the public's right to navigate the water control structure at Laniel, Quebec using the Navigable Waters Protection Act. (see http://www.kipawariver.ca/)
In the now gutted Navigable Waters Protection Act lay the means by which the Minister of Transport could keep the public right of passage down our great Canadian Heritage, our rivers and streams which are threatened especially by resource corporations and power brokers such as Hydro Quebec.
These powerful entities continue to petition that 'this' river or 'that' stream is not navigable and therefore not protectable.
I don't say that dams and bridges should not be built, only that if they are, historical navigation rights should be considered and preserved by making reasonable accommodations for recreational boaters.
It is the Minister of Transport, in exercising the right to allow or disallow work on or over a navigable waterway is what keeps boats and recreational boaters plying our waterways.
To many recent cases launched in the Federal Court concerning the Navigable Waters Protection Act, most recently the case of the Humber Environment Group of Cornerbrook Newfoundland versus the Cornerbrook Pulp and Paper Company indicates that the important oversight is not being faithfully performed. Have we really come to the point now where we must say "such and such a stream is one foot deep, possessing so many cubic feet per second flow and so on?" The answer to this is... YES!
The honourable Mr. Justice John A. O'Keefe, ruled that it had not been shown that the river was navigable. How convenient was that to the Minister? But either the Minister of Transport acts to protect our rivers and streams as a public right or he does not and that means rivers and streams currently enjoyed by kayakers and canoists.
Enough of the cheating, and double-talk. Canadians! our rivers and streams are our own, lets urge the Minister of Transport and the our government to protect them.
Peter Karwacki
In the now gutted Navigable Waters Protection Act lay the means by which the Minister of Transport could keep the public right of passage down our great Canadian Heritage, our rivers and streams which are threatened especially by resource corporations and power brokers such as Hydro Quebec.
These powerful entities continue to petition that 'this' river or 'that' stream is not navigable and therefore not protectable.
I don't say that dams and bridges should not be built, only that if they are, historical navigation rights should be considered and preserved by making reasonable accommodations for recreational boaters.
It is the Minister of Transport, in exercising the right to allow or disallow work on or over a navigable waterway is what keeps boats and recreational boaters plying our waterways.
To many recent cases launched in the Federal Court concerning the Navigable Waters Protection Act, most recently the case of the Humber Environment Group of Cornerbrook Newfoundland versus the Cornerbrook Pulp and Paper Company indicates that the important oversight is not being faithfully performed. Have we really come to the point now where we must say "such and such a stream is one foot deep, possessing so many cubic feet per second flow and so on?" The answer to this is... YES!
The honourable Mr. Justice John A. O'Keefe, ruled that it had not been shown that the river was navigable. How convenient was that to the Minister? But either the Minister of Transport acts to protect our rivers and streams as a public right or he does not and that means rivers and streams currently enjoyed by kayakers and canoists.
Enough of the cheating, and double-talk. Canadians! our rivers and streams are our own, lets urge the Minister of Transport and the our government to protect them.
Peter Karwacki
Tabaret is a Bad Idea (Part Three)
10 Reasons WhyTabaret is a Bad Idea1) Tabaret is too big. The station is designed to useevery drop of water available in the Kipawawatershed, but will run at only 44 percent capacity.We believe the Tabaret station is designed to usewater diverted from the Dumoine River into theKipawa watershed in the future.
2) The Tabaret project will eliminate the aquaticecosystem of the Kipawa River.The Tabaret project plan involves the diversion of a16-km section of the Kipawa River from its naturalstreambed into a new man-made outflow from LakeKipawa.
3) Tabaret will leave a large industrial footprint on thelandscape that will impact existing tourismoperations and eliminate future tourism potential.
4) The Tabaret project is an aggressive single-purposedevelopment, designed to maximize powergeneration at the expense of all other uses.
5) River-diversion, such as the Tabaret project, takinglarge amounts of water out of a river’s naturalstreambed and moving it to another place, is verydestructive to the natural environment.
6) The Kipawa River has been designated a protectedgreenspace in the region with severe limitations ondevelopment. This designation recognizes theecological, historical and natural heritage value ofthe river and the importance of protecting it.Tabaret will eliminate that value.
7) If necessary, there are other, smarter and morereasonable options for producing hydro power onthe Kipawa watershed. It is possible to build a lowimpactgenerating station on the Kipawa river, andmanage it as a “run-of-the-river” station, makinguse of natural flows while maintaining other values,with minimal impact on the environment.
8) The Kipawa watershed is a rich natural resource forthe Temiscaming Region, resonably close to largeurban areas, with huge untapped potential fortourism and recreation development in the future.Tabaret will severely reduce this potential.
9) Tabaret provides zero long-term economic benefitfor the region through employment. The plan is forthe station to be completely automated andremotely operated.
10) The Kipawa River is 12,000 years old. The riverwas here thousands of years before any peoplecame to the region. The Tabaret project will change all that.
Problems on a local River?
- There is more to do as well but you have to do your research and above all, don't give up.
- IN the meantime prepared a document itemizing the history of navigation of this spot and its recreational value. Use the Kipawa river history of navigation as a guide: see www.kipawariver.ca
- Under the Ministry of Environment guidelines you have a set period of time to petition the change under the environmental bill of rights, you may have limited time to take this action. But it involves going to court for a judicial review of the decision.
- 4. contact the ministry of natural resources officials and do the same thing.
- 3. contact the ministry of the environment and determine if they approved the project
- 2. determine if the dam was a legal dam, approved under the navigable waters protection act.
- 1. research the decision and timing of it to determine if an environmental assessment was done.
Minden Ontario

Gull River Water control at Horseshoe lake
A History of Navigation on the Kipawa River
Prior to the environmental assessment there was no signage at the Laniel Dam
T-Shirts Area: These are available now!

Send $25 and a stamped self addressed envelop for the Tshirt, and for the bumper sticker, a stamped and self addressed envelope with $5.00 for the bumper sticker to Les Amis de la rivière Kipawa, 80 Ontario St., Ottawa, Ontario, K1K 1K9 or click the link To purchase a Les Amis "T" contact Doug with the following information: Number of shirts:Sizes: Ship to Address: Method of Payment: cash, cheque and paypal, Shipto address:
Bumper Stickers Now Available

Get your bumper sticker and show your support for the Kipawa Legal Fund ! - send $5.00 in a Stamped, self addressed envelope to: Peter Karwacki Box 39111, Ottawa, Ontario, Canada, K1H 7X0
















